Event logs contain important information for use in troubleshooting and information security investigations. Infrastructure and security teams should make make a conscious decision about retention of their important event logs so data is available on an endpoint when needed. The easiest way to set retention is to specify a max file size for the event log. After reaching this size, the oldest events will be overwritten with new.
Setting the max size of the standard Application, Security, Setup, and System event logs via GPO to standardize the settings across a domain is easy. But setting the max size for other logs, such as those under Applications and Services Logs → Microsoft within Event Viewer, is not as straight forward.
Standard log sizes
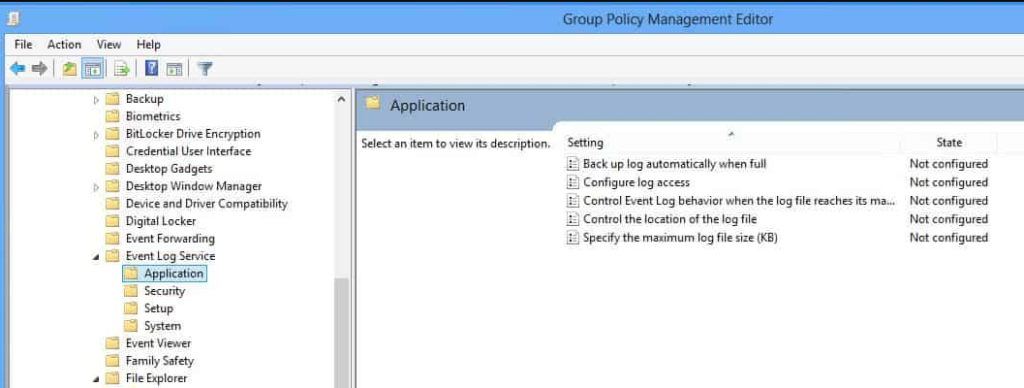
To set the size of the standard four event logs, open the Group Policy Management Editor, browse to Computer Configuration → Policies → Administrative Templates → Windows Components → Event Log Service. Select the log you need then change the Specify the maximum log file size setting.
Other logs
There is no built-in setting in the GPO editor for changing the max size of all the other event logs, such as those under Applications and Services Logs → Microsoft within Event Viewer. Instead, a registry key needs to be manually set via GPO to control these sizes.
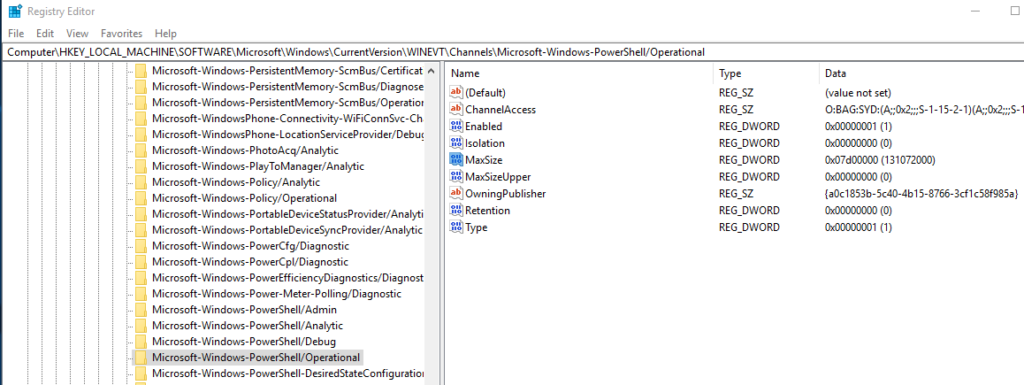
The MaxSize value name under HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\WINEVT\Channels\ is what you want. Here is the value for setting the PowerShell Operational log to a size of 128MB. This particular log can be configured to record details of PowerShell execution that would be helpful during incident response:
Once you know what size you want , configure your group policy to add/modify the registry key and value. Here is a comprehensive guide showing how to configure: https://theitbros.com/add-modify-and-delete-registry-keys-using-group-policy/
Apply and Validate
After the sizes are set, link the group policy to the OU/machines that need it. Then run gpupdate /force or reboot the workstations to pick up the configuration.
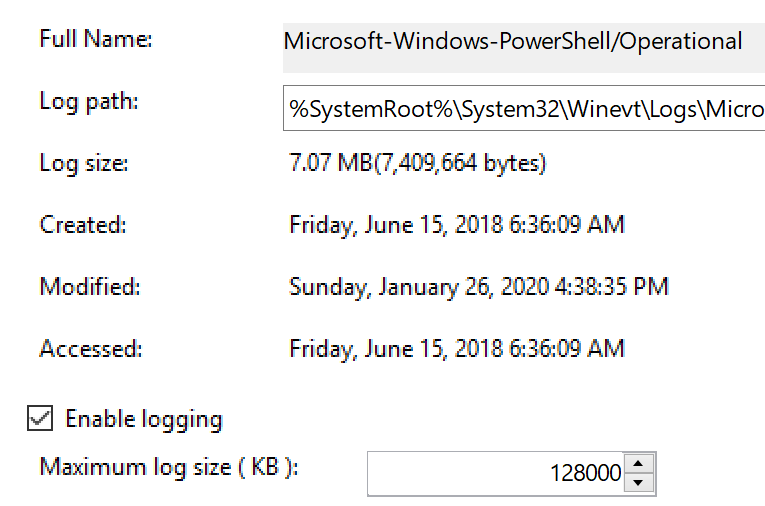
You can validate your setting took effect on an endpoint by right clicking the event log in Event Viewer, selecting Properties, and checking the maximum log size.
Of course, it is possible to clear event logs manually. A bad actor that gains access to a machine may try to clear the logs to cover their tracks. A way to retain log data even after the logs are cleared is to use Windows Event Forwarding to send important logs to a SIEM in near real time for longer term retention and centralized searching. More on that in the future.